Security Hierarchy Maintenance
This process allows you to maintain the Security Hierarchy.Overview:
This process allows you to maintain the Security Hierarchy. The Security Hierarchy defines your companys' structure and is the first step required when implementing the Role Based Security scheme. The hierarchy consists of Database, Department, Workgroup, Role and finally Users. At each level you can specify inactivity and timeout values. Timeout refers to the length of time in minutes after which an inactive session will be logged out. Inactivity refers to the number days since last login, after which the user will not be allowed to log on. The Timeout and Inactivity values do not apply while you are running System Administration, Database Management, and Application Design in order to prevent accidental lockouts. The Timeout value respects the Process level setting for Cancel OK=N and the Child level setting for Cancel Disposition=DISABLE. If it encounters these set on a process then that process will not auto-logout. Setting the keyboard timer for a process also deactivates the auto logout timer for that process for as long as the keyboard timer is set to a non-zero value. When a auto logout timer expires it fires Option Intercept with --- OPTION = LOGOUT so you have one more chance to intercept the auto-logout and stop it by changing the value of --- OPTION to something else. A configuration setting controls whether or not users can belong to more than one Role at a time. You may wish to set that before defining your hierarchy. See Setting RBS Configuration. After defining the hierarchy, you may want to print it via Security Hierarchy List/Export on the 'Reports' tab of the RBS menu. You can copy the Hierarchy, so if you have a multiple databases, it is not necessary to define each database individually. Define the first hierarchy, then use the Copy Security program on the 'Utilities' tab of the RBS menu to set up your other databases. There are also utilities to export and import the hierarchy, which can be used to transfer the hierarchy to another machine. Caution: If you delete something from the Hierarchy, the Access Control Lists associated with that element will be lost. You cannot restablish the ACL, even if you add back the deleted element with the same name or user id. You will have to set up the ACL again, using Set Process Security and Set File/Field Security. Here is an example of how a simple Security Hierarchy might look.-
Database : ACME Insurance, Inc. (APPX Database AAA)
-
Department: Sales
-
Workgroup: New Sales
-
Role: Manager
-
User: John Rogers (APPX User JR)
-
-
Role: Inside Rep
-
User: William Smith (APPX User WS)
-
User: Samuel Adams (APPX User SA)
-
-
-
Workgroup: Administration
-
Role: Manager
-
User: Mary Jones (APPX User MJ)
-
-
Roles: Clerical (APPX User BS)
-
User: Brenda Starr
-
-
-
-
Department: Claims
-
Workgroup: Administration
-
Role: Manager
-
User: Bruce Williams
-
-
Role: Clerical
-
User: Wanda Scott
-
-
-
-
Description:
When you run 'Security Hierarchy Maintenance' you will see the following screen: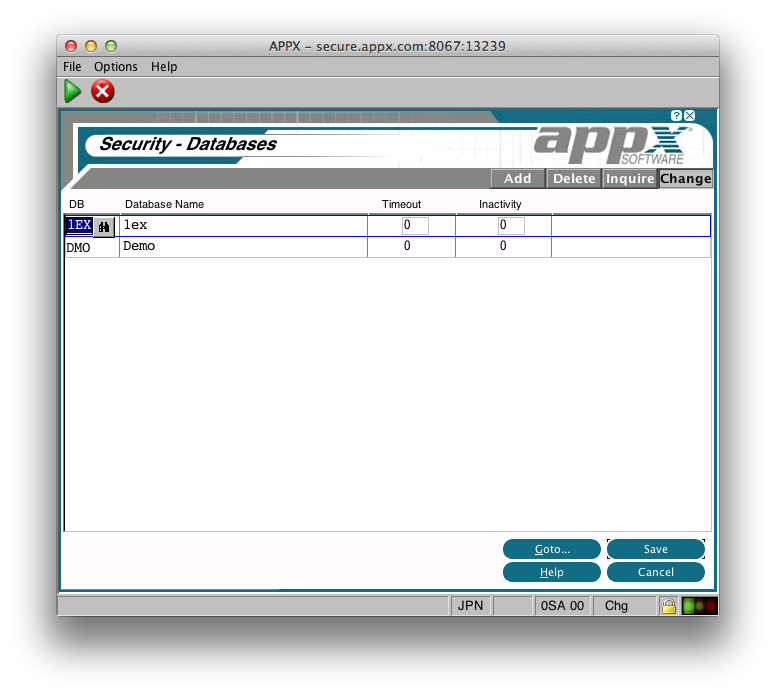 The Database Id must refer to a Database you have defined in Appx System Administration. You can also set the Timeout and Inactivity settings here. When you press Enter, you will be taken to the 'Department' level:
The Database Id must refer to a Database you have defined in Appx System Administration. You can also set the Timeout and Inactivity settings here. When you press Enter, you will be taken to the 'Department' level:
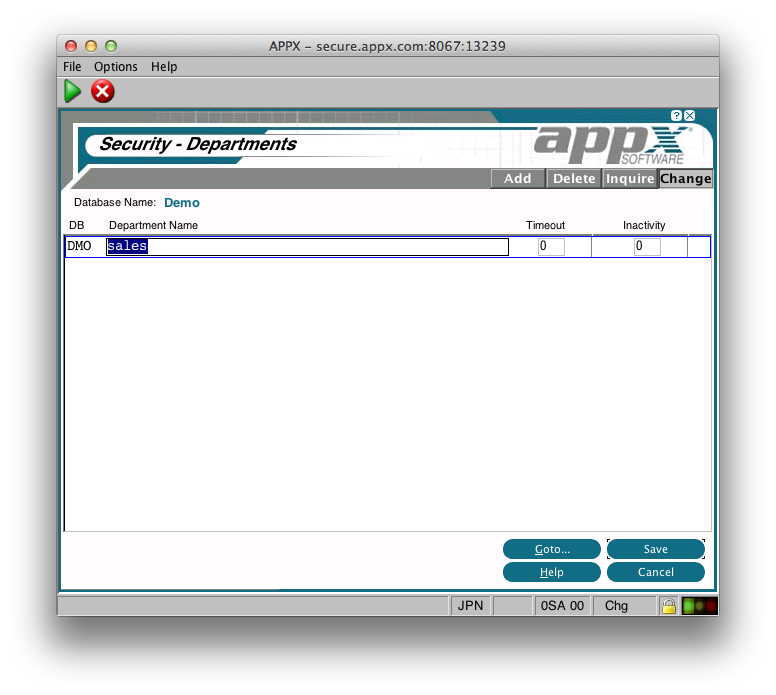 Here you define the Departments within the selected Database. Department names must be unique within the Database. A Timeout and Inactivity setting can also be specified at this level. When you press Enter, you will be taken to 'Workgroups' for the Department:
Here you define the Departments within the selected Database. Department names must be unique within the Database. A Timeout and Inactivity setting can also be specified at this level. When you press Enter, you will be taken to 'Workgroups' for the Department:
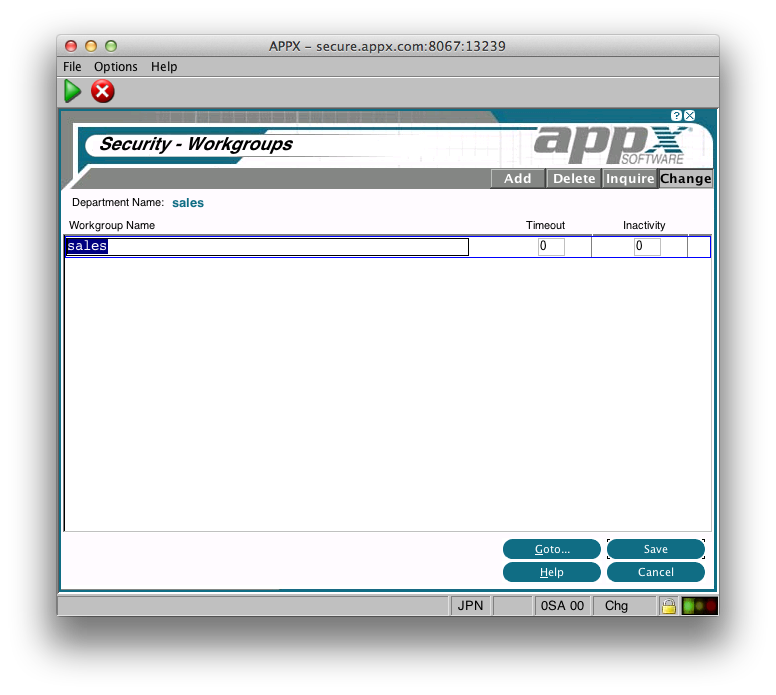 As with Departments, you can specify the Timeout and Inactivity settings. Workgroup names must be unique within the Department. When you press Enter, you will be taken to the 'Roles' for the Workgroup:
As with Departments, you can specify the Timeout and Inactivity settings. Workgroup names must be unique within the Department. When you press Enter, you will be taken to the 'Roles' for the Workgroup:
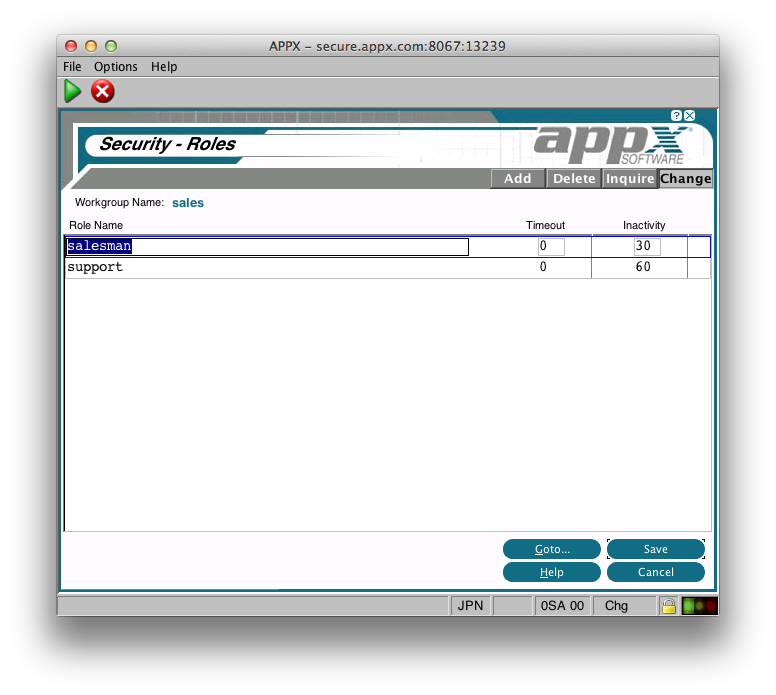 Again, we have options for the Timeout and Inactivity settings. Roles must be unique within a Workgroup. When you press Enter, you will be taken to 'Users':
Again, we have options for the Timeout and Inactivity settings. Roles must be unique within a Workgroup. When you press Enter, you will be taken to 'Users':
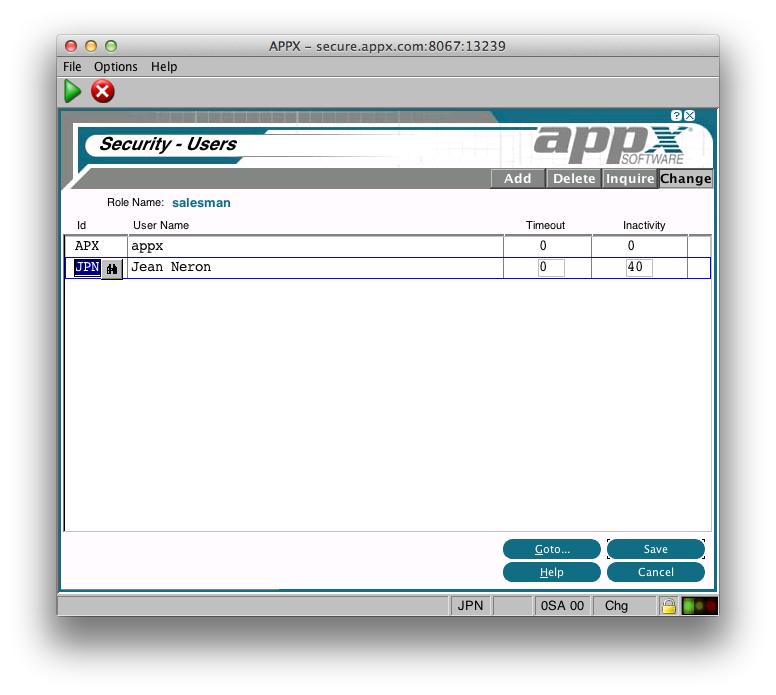 This is the lowest level in the hierarchy and the timeout/inactivity settings here will take priority over higher levels. The user must be defined in Appx System Administration.
This is the lowest level in the hierarchy and the timeout/inactivity settings here will take priority over higher levels. The user must be defined in Appx System Administration.
Comments:
Read what other users have said about this page or add your own comments.-- JeanNeron - 2012-11-01
Ideas, requests, problems regarding TWiki? Send feedback

