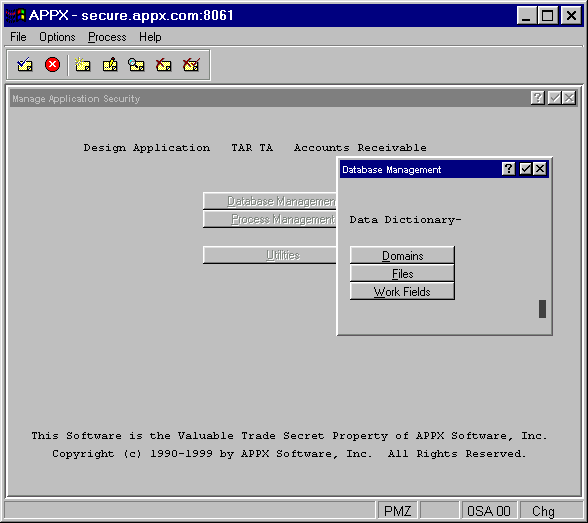
When you select Database Management from the 'Manage Application Security' menu, the Database Security Management overlay shown in Figure 5-2 appears:

Figure 5-2. Database Security Management Overlay
The options on the Database Security Management overlay provide access to security for the different types of database items as follows:
· Domains
These options are described in detail later in this manual. In general, however, when you select an option, a list of all items of that particular type in the selected application displays. From this list you can define “read” and “modify” rights for every item on the list by placing your cursor on the row containing the item name. In general, a Read right lets a user see the contents of a field, but not change it; a Modify right lets a user change the contents of a field. Modify rights always include Read rights.
There is a hierarchy in assigning security rights to fields. If a field is a domain type field and its domain is assigned a security code, no security code can be assigned to the field itself. If no security code is assigned to the domain, a security code can be assigned to the field. If a field is not secured by domain or field security, it is subject to the security code assigned at the file level which provides security to all unsecured fields in that file. If no security codes are assigned at any of these levels, access to the field is unrestricted.