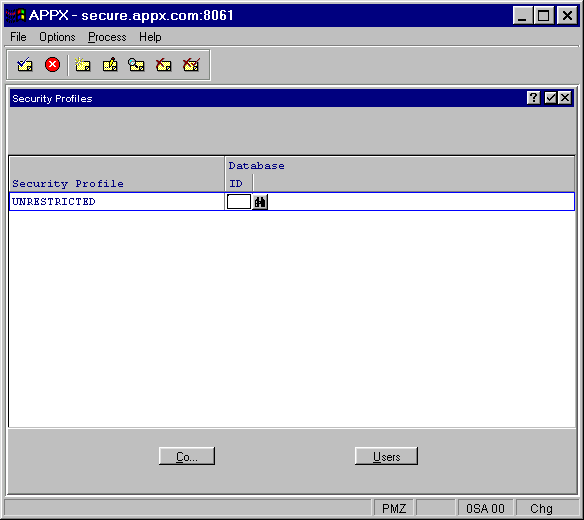
The Users Security Profiles overlay accessed from the Users File Maintenance screen is shown in Figure 2-49 below. It runs Security Profiles File Maintenance but constrains it to the user's security profile (which was specified in the Users File Maintenance overlay). This allows you to view and/or edit security rights for that profile and its associated databases. Note, however, to set up new security profiles or to avoid constraints, you should run Security Profiles File Maintenance from the Security menu.

Figure 2-49. Users Security Profiles Overlay
The Users Security Profiles overlay contains the following items:
· Security Profile identifies the security profile currently specified for this user.
· Database ID identifies a valid database associated with this security profile. When a user that has a security profile selects a database, APPX first tries to find a record for the specified profile/database combination. If the combination cannot be found, APPX uses the profile with a blank database ID.
See Security Profiles File Maintenance for a complete description of the options and overlays associated with this screen.