
Difference: TWikiAccessControl (40 vs. 41)
Revision 412013-10-09 - TWikiContributor
| Line: 1 to 1 | |||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
TWiki Access Control | |||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||
| > > | |||||||||||||||||||||||||||||||||||||||||||||||||
| Restricting read and write access to topics and webs, by Users and groups TWiki Access Control allows you restrict access to single topics and entire webs, by individual user and by user Groups. Access control, combined with TWikiUserAuthentication, lets you easily create and manage an extremely flexible, fine-grained privilege system. | |||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 12 to 13 | |||||||||||||||||||||||||||||||||||||||||||||||||
An Important Control Consideration | |||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Open, freeform editing is the essence of WikiCulture - what makes TWiki different and often more effective than other collaboration tools. For that reason, it is strongly recommended that decisions to restrict read or write access to a web or a topic are made with great care - the more restrictions, the less Wiki in the mix. Experience shows that unrestricted write access works very well because: | ||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Your organization will learn that, while fostering an open collaborative environment, soft security (peer review), together with version control (complete audit trail) will take care of any security concern you might have. Open, free-form editing is the essence of WikiCulture - what makes TWiki different and often more effective than other collaborative environments. For that reason, it is strongly recommended that decisions to restrict read or write access to a web or a topic are made with great care - the more restrictions, the less wiki in the mix. Experience shows that unrestricted write access works very well because: | ||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 23 to 26 | |||||||||||||||||||||||||||||||||||||||||||||||||
Permissions settings of the webs on this TWiki site | |||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Note: Above table comes from SitePermissions | ||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Note: Above table comes from SitePermissions | ||||||||||||||||||||||||||||||||||||||||||||||||
Authentication vs. Access Control | |||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 128 to 132 | |||||||||||||||||||||||||||||||||||||||||||||||||
For example, set this to restrict a topic to be viewable only by the MarketingExecGroup:
| |||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Remember when opening up access to specific topics within a restricted web that other topics in the web - for example, the WebLeftBar - may also be accessed when viewing the topics. The message you get when you are denied access should tell you what topic you were not permitted to access. | ||||||||||||||||||||||||||||||||||||||||||||||||
| > > | See "How TWiki evaluates ALLOW/DENY settings" below for more on how ALLOW and DENY interacts. | ||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Be careful with empty values for any of these. | ||||||||||||||||||||||||||||||||||||||||||||||||
| > > | |||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
Allowing public access to specific topics in a restricted web | ||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||
| > > | You may want to completely open up access to a specific topic within a restricted web - allowing access by anybody. There is a special group for that - Main.AllUsersGroup. The following setting allows view access to the topic by anybody even if they are not authenticated.
| ||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||
| < < | The same rules apply to ALLOWTOPICCHANGE/DENYTOPICCHANGE and APPLYTOPICRENAME/DENYTOPICRENAME. Setting ALLOWTOPICCHANGE or ALLOWTOPICRENAME to en empty value means the same as not defining it. Setting DENYTOPICCHANGE or DENYTOPICRENAME to an empty value means that anyone can edit or rename the topic. | ||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Alternatively, you can grant access only to authenticated users by Main.AllAuthUsersGroup. If an unauthenticated user accesses a topic having the following setting, they are asked to authenticate themself.
| ||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||
| < < | |||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Remember when opening up access to specific topics within a restricted web that other topics in the web - for example, the WebLeftBar - may also be accessed when viewing the topics. The message you get when you are denied access should tell you what topic you were not permitted to access. | ||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||
| < < | |||||||||||||||||||||||||||||||||||||||||||||||||
| > > | As mentioned in the following section, meaning of an empty value set to DENYTOPICVIEW, DENYTOPICCHANGE, and DENYTOPICRENAME has been changed in TWiki 6.0.
To keep those TWiki topics having empty DENYTOPICOPERAION accessible by everybody, those need to be replaced with
| ||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||
| < < | See "How TWiki evaluates ALLOW/DENY settings" below for more on how ALLOW and DENY interacts. | ||||||||||||||||||||||||||||||||||||||||||||||||
| > > | For that, tools/eliminate_emptydenytopic is provided.
After upgrading from pre 6.0 to post 6.0, you need to run it.
Empty values in access control variablesSetting an empty value to an access control variable is the same as not setting at all:
| ||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 185 to 202 | |||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 198 to 215 | |||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Allowing web creation by user mapping managerThere are cases where DENYROOTCHANGE, ALLOWROOTCHANGE, DENYWEBCHANGE, and ALLOWWEBCHANGE, and DENYWEBCHANGE are not capable enough to implement web creation permission you want. To cope with such cases, when a new web is created, thecanCreateWeb($cUID, $web) method of the user mapping manager is called if the method exists.
If it returns true, TWiki goes ahead and create the web without checking access control variables.
Please read AllowWebCreateByUserMappingManager for more details.
User masqueradingThere are cases where it's handy to access TWiki on behalf of somebody else retaining a trace of your real identity rather than completely becoming a different user. We call it user masquerading. TWiki provides a framework to implement that. Please read UserMasquerading for more information. This is an advanced feature and not many TWiki sites are using, but there is a part in the following section mentioning it, it's mentioned here.Dynamic access controlThis feature is regarded experimental. There are pitfalls and vulnerability. Before using this feature, please read this entire section through carefully. You may want to restrict access dynamically -- based on topic name, a form field value, or some combination of factors. To cope with such situations, the dynamic access control mechanism is provided. If you setDYNAMIC_ACCESS_CONTROL 'on' at WebPreferences of the web, TWiki variables in access control variables mentioned above are expanded.
Example 1 - restriction based on topic nameLet's assume you need to restrict changes only to the CroniesGroup members excep with topics whose name ends with Public, which need be changed by anybody. That is achieve by the following settings on WebPrefences.
* Set DYNAMIC_ACCESS_CONTROL = on
* Set ALLOWWEBCHANGE = %IF{"'%CALCULATE{$SUBSTRING(%TOPIC%, -6, 6)}%' = 'Public'" then="%WIKINAME%" else="CroniesGroup"}%
Example 2 - restriction based on form fieldLet's assume:
* Set DYNAMIC_ACCESS_CONTROL = on
* Set ALLOWWEBVIEW = %IF{"'%CALCULATE{$SUBSTRING(%TOPIC%, 1, 6)}%' = 'ReqEnt' and '%FORMFIELD{Requestor}%' != '%WIKINAME%'" then="SupportGroup" else="%WIKINAME%"}%
Specifically the following access control variables are subject to TWiki variable expansion in their values.
Dynamic access control in accessing a different web's topicLet's assume WebA has the following lines on WebPreferences.* Set DYNAMIC_ACCESS_CONTROL = on * Set MEMBERS = JaneSmith, JoeSchmoe * Set ALLOWWEBVIEW = %MEMBERS%This is not a good way to use dynamic access control but it does restrict accessonly to those listed in MEMBERS. However, access control doesn't work as expected when WebA.TopicB is accessed from WebC.TopicD by %INCLUDE{WebA.TopicB}% or other variables.
This is because %MEMBERS% is defined in WebA and may have a different value in other webs.
You may think the following lines cheat the access control on WebA but actually not.
* Set MEMBERS = %WIKINAME%
%INCLUDE{WebA.TopicB}%
This is because when a topic (e.g. WebC.TopicD) is accessed from browser and the topic refers to another topic in a different web (e.g. WebA.TopicB) and the different web employs dynamic access control, access to another topic is defined being on the safer side.
Topic level dynamic access controlOn a topic, it's possible to use a variable defined on the topic for topic level access restriction. E.g.* Set MEMBERS = JaneSmith, JoeSchmoe * Set ALLOWTOPICVIEW = %MEMBERS%[This is not a good way to use dynamic access control Dynamic access control and user masqueradingYour user mapping handler may be providing the UserMasquerading feature. In that case, you expect dynamic access control to just work when user masquerading is in effect. Otherwise, you cannot test if your dynamic access control configuration is working as expected on your own. Dynamic access control does work as expected even if user masquerading is in effect. For that, the following things are happening under the hood. Let's think about Example 2 mentioned above. When you masquerading as SomebodyElse, you need to be able to see SomebodyElse's requests only. In the access control setting, a form field value is compared with %WIKINAME%. While user masquerading is in effect, your wiki name is YourNameOnBehalfOfSomebodyElse. It cannot match the form field value. To make dynamic access control work under these circumstances, variable expansion for dynamic access control is skewed as follows. Specifically, the following variables are expanded to the value of SomeboyElse's rather than YourNameOnBehalfOfSomebodyElse's.
VulnerabilityIt's possible to redefine function tags such as %IF{...}% in your personal preferences. In a future release of TWiki, a way to prevent function tags from being overridden by personal preferences will be provied. But until then, you need to be well aware of this vulnerability.Disabling dynamic access controlYou may not be comfortable with dynamic access control because it may slow things down. Or you may not want to be bothered by questions raised by users about it. If so, you can disable it by setting DYNAMIC_ACCESS_CONTROL 'off' and then finalizing at the local site level. (cf. TWikiVariables#Setting_Preferences_Variables) | ||||||||||||||||||||||||||||||||||||||||||||||||
Access control and INCLUDEALLOWTOPICVIEW and ALLOWTOPICCHANGE only applies to the topic in which the settings are defined. If a topic A includes another topic B, topic A does not inherit the access rights of the included topic B. | |||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 207 to 338 | |||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Customizing "access denied" messageWhen access is denied, a page as follows is displayed: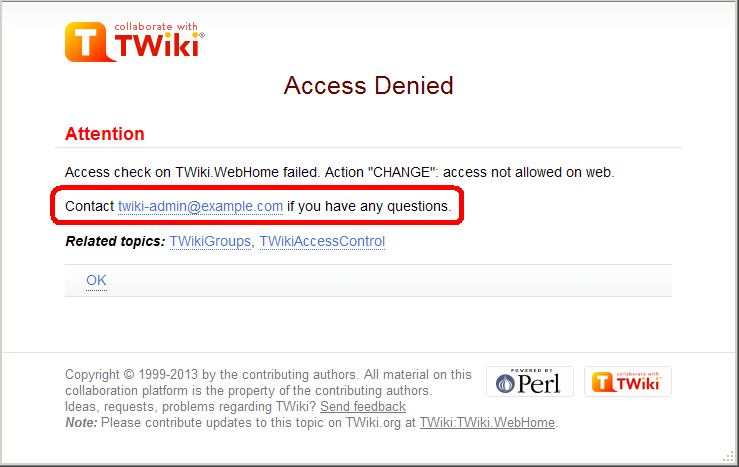 You may want to customize the passage annotated in the red rectangle.
For example, with a web restricting access, you may want to show the link to an access request form.
You can achieve that by setting
You may want to customize the passage annotated in the red rectangle.
For example, with a web restricting access, you may want to show the link to an access request form.
You can achieve that by setting TOPIC_ACCESS_CONTACT varialbe on WebPreferences. e.g.
* Set TOPIC_ACCESS_CONTACT = If you need to access this site, please apply [[Main.AccessForm][here]]Please note that setting it on a topic other than WebPreferences does not take effect. This is a limitation of the current implementation. Custom user/group notationsYou can have custom user/group notations such asUSER:userid and LDAPGROUP:group-name and use them for access control. For example:
* Set ALLOWWEBCHANGE = UID:buzz, LDAPGROUP:foo-barIn a large organization, TWiki may need to depend on user and group data provided by its infrastructure. Custom user/group notations are handy in such situations though it's not trivial to implement. Please read here for details. | ||||||||||||||||||||||||||||||||||||||||||||||||
Access Control quick recipes | |||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 284 to 441 | |||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Related Topics: AdminDocumentationCategory, TWikiUserAuthentication, TWiki:TWiki.TWikiAccessControlSupplement | ||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Related Topics: AdminDocumentationCategory, TWikiUserAuthentication, AllowWebCreateByUserMappingManager, UserMasquerading, CustomUserGroupNotations, TWiki:TWiki.TWikiAccessControlSupplement | ||||||||||||||||||||||||||||||||||||||||||||||||
|
-- Contributors: TWiki:Main.PeterThoeny | |||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||
View topic | History: r42 < r41 < r40 < r39 | More topic actions...
Ideas, requests, problems regarding TWiki? Send feedback
Note: Please contribute updates to this topic on TWiki.org at TWiki:TWiki.TWikiAccessControl.